These monitoring systems collect data from and about the assets and send periodic reports to the analytics engine. Wishing for a unique insight into a subject matter for your subsequent individual research.
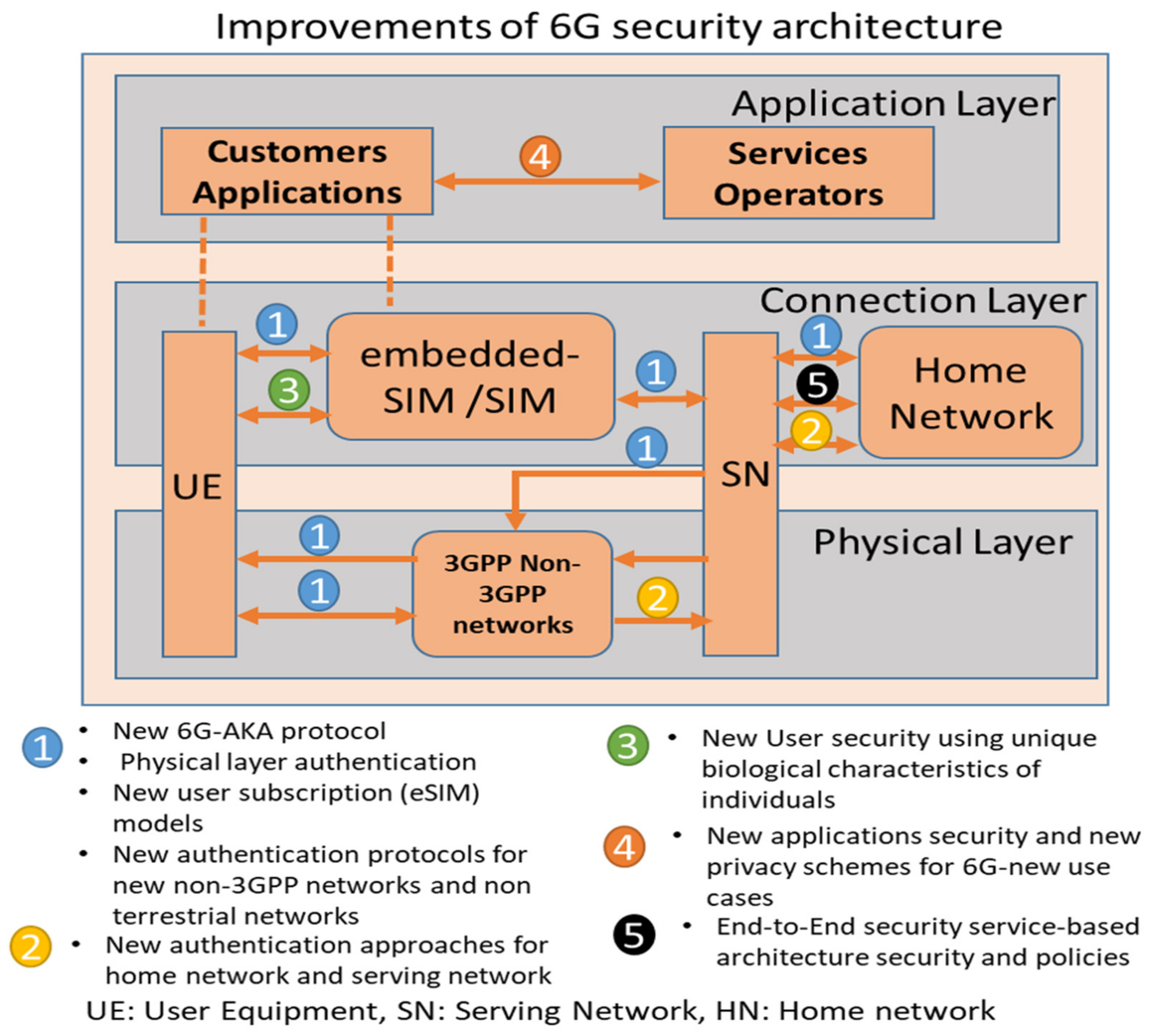
Sensors Free Full Text Security Requirements And Challenges Of 6g Technologies And Applications Html
We do not at any time disclose clients personal information or credentials to third parties.

. Therefore a security professional should have a strong UNIX and Linux background. We have writers with varied training and work experience. They can also be used to scan for known vulnerabilities and scan VMs BYOD devices and client databases.
You can use this feature to combine endpoint criteria to satisfy your requirements before the ASA assigns a specific dynamic access policy DAP to the session. Many of these tools are UNIX or Linux based. Reviewing raw scan results is a labor-intensive task.
Since emerging in 2007 as a banking Trojan Qakbot has evolved into a multi-purpose. Endpoint Assessment is a HostScan extension that examines the remote computer for a large collection of antivirus and antispyware applications associated definitions updates and firewalls. ET 111 DC-System 4 Credits.
JTAG named after the Joint Test Action Group which codified it is an industry standard for verifying designs and testing printed circuit boards after manufacture. This course introduces the theory and application of passive direct current circuits. Who Works in Our Academic Writing Service.
The assets within the enterprise are monitored using installed agents that reside on the asset as well as network-based monitoring systems that scan and capture network traffic. Dynamic application security testing DAST DAST examines a target applications code to identify its attack. We give anonymity and confidentiality a first priority when it comes to dealing with clients personal information.
Multiple Qakbot campaigns that are active at any given time prove that the decade-old malware continues to be many attackers tool of choice a customizable chameleon that adapts to suit the needs of the multiple threat actor groups that utilize it. Control in PIECES framework recognizes if the current method of operation offer effective controls to ensure against scam and to ensure accuracy and security of information and data. By using our website you can be sure to have your personal information secured.
Brad Lynch sadlyitsbradley. We provide solutions to students. It specifies the use of a dedicated debug port implementing a serial.
Your favorite homework help service. I would love to go into my spiel about how I originally believed SeaCliff was a Quest Plus and SeaBright was a Quest Pro but my render has brought a lot of confusion toward people in the know Talking to these people I might have seen something even further than this year. 2P Pancake vs.
JTAG implements standards for on-chip instrumentation in electronic design automation EDA as a complementary tool to digital simulation. This ends up becoming the bottleneck for traditional SAST tools. To that end the Internet edge is designed with security in mind where multiple security technologies and capabilities are strategically deployed throughout the network to complement each other and to collaborate.
This course covers the basic principles of Computer-Aided Design CAD and drafting. Examples of tools include Nipper Secunia PSI Core Impact Nessus v6 SAINT and Open VAS. Your security team or development leads need to validate and prioritize true positives while removing false positives.
Workspace ONE Unified Endpoint Management UEM powered by AirWatch includes. Using the CAD system allows hands-on experience in learning how to create prepare store and retrieve technical drawings and related information. Effective network security demands the implementation of various security measures in a layered approach and guided under a common strategy.
One assignment at a time we will help make your academic journey smoother. As you design your Workspace ONE components learn how to use Workspace ONE UEM to be responsible for device enrollment a mobile application catalog policy enforcement regarding device compliance and integration with key enterprise services such as email content and social media. The current sense amp outputs either a voltage or a current that is proportional to the current through the measured path.
Please Use Our Service If Youre. D Flip-Flop A D or Delay Flip Flop Figure 1 is a digital electronic circuit used to delay the change of state of its output signal Q until the next rising edge of a clock timing input signal occurs.

Ccna 3 V7 0 Curriculum Module 3 Network Security Concepts

Ceh V11 笔记总结module 5 违规用户 的博客 Csdn博客
Pdf Penetration Testing Active Reconnaissance Phase Optimized Port Scanning With Nmap Tool
0 Comments